![]()
http://www.codepoetry.net/ Copyright © 2001 – 2005 codepoetry.net
First posted on:
http://www.macgeekery.com/tips/security/basic_mac_os_x_security
Basic Mac OS X Security
by Adam Knight aka CodePoet
Well, now that we have a possible candidate for another Mac Trojan[1] (not a virus, not a worm, not an exploit, and not good code[2]) I think now's as good a time as any to cover some basic Mac OS X Security so that people not familiar with such things have more than an ice cube's chance in Phoenix at keeping secure.
Mac OS X is a secure operating system in that it's multi-user and has limits on what some user accounts can do. If an account is setup as a basic user, that user can only hurt himself, not the whole system or other users. However, in the interest of being "friendly" to new users, Apple leaves of a lot of the secure bits off for the first user created and this means that Trojans like this week's can cause some pretty nasty problems on your system.
Yet, all of this is easy to correct. Just run over the following and you should be well on your way to a protected computer.
Rule #1: The Administrator is Not for Daily Use
![]() Contrary
to what Apple does with the setup program, the administrator account is not
viable for daily use. There are too many things this account can do that you
don't want a script to be able to, such as cleaning out /Applications or
various folders within /Library.
Contrary
to what Apple does with the setup program, the administrator account is not
viable for daily use. There are too many things this account can do that you
don't want a script to be able to, such as cleaning out /Applications or
various folders within /Library.
Instead:
· Go make another account in System Preferences
· Make it an administrator
· Login with the new account and remove administrator rights from your original account
· Log back in with the original account
Now when you're prompted to enter a password to do something stupid creative, use the admin account name. This has the added benefit
that people that walk up to your computer can't do bad things to the system,
either (just your account, so keep reading).
 Rule
#2: System Preferences is Not for Daily Use
Rule
#2: System Preferences is Not for Daily Use
You can do some crazy stuff in System Preferences. Happily, Apple realized this and added some settings to protect the system from random idiots (driver or passengers). You'll want to use these to lock System Preferences out to roaming users that happen to get a hold of your computer. Open System Preferences and go to the Security pane. Review the following as you make the changes.
· Require password to wake this computer from sleep or screen saver: This does exactly what it says. If you put the computer to sleep or have a screen saver setup then you'll be asked for your user account information to unlock the computer. Use this, especially on portables. Of course, a restart will make this go away, so ...
· Disable automatic login: This completely disables automatic login. Your system will startup to a login panel with a list of names. This is the most secure option because it doesn't make the computer usable from a cold boot. If you know the system will log you in as a user with a restart, any security measure meant to prevent someone from having user-level access can be defeated with a reboot. Turn this on to prevent that.
· Require password to unlock each secure system preference: Notice how a lot of preferences have that lock at the bottom (like Network, Security, and Accounts)? Turning this on locks all of those by default, requiring an admin password (even for the admin user) to unlock. If you don't do this, anyone can come right back to this preference pane and turn all of these settings off. Check it.
· Log out after __ minutes of inactivity: More annoying than useful to me, but if you tend to walk away from your computer and don't mind losing your place in your work, turn this on. Locking the screensaver works well for me, instead.
· Use secure virtual memory: Turn this on. If this is off, then any time you enter a password it's possible the system will write that password out in a block of memory it's dumped to a file in /var/vm and, thus, makes the password recoverable. Using secure VM means those files are encrypted and it's near-impossible to discover a user's password from the swap files.
Rule #3: Turn off Services You Do Not Use
Go to System Preferences, then Sharing. Uncheck everything you're not using, even if you think you will. Turn it on when you need it and turn it off when you're done.
Rule #4: Secure Secure Shell
By default, SSH allows SSH v1, listens on the default port, and allows anyone with an account remote access. Secure, my ass. Change the port and limit the users allowed to users that need it. In /etc/sshd_config change:
- #Port 22
+ Port 2200
- #Protocol 2,1
+ Protocol 2
- #PermitRootLogin yes
+ PermitRootLogin no
That moves ssh to port 2200, prevents root from logging in remotely (presuming you set a password for root, which you should not), and forces the more secure v2 protocol without a fallback. The only change you'll need to remember is to connect to your machine as follows, instead:
$ ssh -p 2200 myuser@myhost.local
Now, we need to restrict the users that can login (your other users will unlikely ever need to ssh in, including that admin you made previously).
AllowUsers codepoet
Now only I can login to my machines. Replace the username as appropriate, or make me an account and tell me your IP address.
Update: As mentioned on CIPB[3] the port change happens in /etc/services, not in /etc/sshd_config because launchd is starting sshd rather than it running as a daemon. Change /etc/services as follows:
- ssh 22/tcp
+ ssh 2200/tcp
 Rule
#5: Outbound Calls Only, Please (Firewall)
Rule
#5: Outbound Calls Only, Please (Firewall)
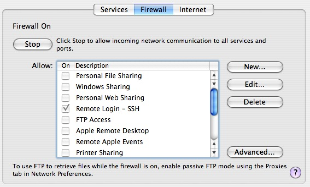
Some look at Apple's firewall as useless because it automatically pinholes running services and doesn't allow some users in while locking some users or or whatnot. It's not a commercial-level firewall (GUI) but it does do something very well: it prevents ports opened by rootkits or trojans from being accessible. Turn on the firewall and unauthorized listeners will be blocked.

It also makes our SSH hack above useless by blocking 2200 by default. Click on New and pick Other from the menu and add 2200 as an option and check it and any other services you want to offer.
 Rule
#6: Freeze the Credit Card (Keychain)
Rule
#6: Freeze the Credit Card (Keychain)
 The
Keychain is the most dangerous moment of brilliance I've ever seen. On one
side, it knows your passwords to everything and lets you get away with being
human while still being secure. On the other, it lets you get away with being
human while being insecure. If you walk away, I can connect to just about any
password-protected service you have access to and the computer will fill in the
password for me.
The
Keychain is the most dangerous moment of brilliance I've ever seen. On one
side, it knows your passwords to everything and lets you get away with being
human while still being secure. On the other, it lets you get away with being
human while being insecure. If you walk away, I can connect to just about any
password-protected service you have access to and the computer will fill in the
password for me.
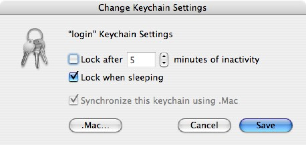
Yet, it has controls (again, turned off by default) that let you get around this. In Keychain Access, go to Edit and then to Change Settings for Keychain. You can do two things here: set an idle timeout, or tell it to lock on sleep. I prefer just locking on sleep, myself, because I rather depend on the screensaver to do the idle locking for my systems. Sleep, however, especially for portable users, means that the person waking the computer may or may not be the owner, and that's prime time to start asking for passwords. Until a password is entered you won't be on IM, or checking mail, or whatever else. Programs that use passwords will be locked from getting new data.
If your keychain password is different from your account password then you have an even greater level of security as the screensaver password won't work for the keychain, and vice-versa.
Rule #7: Make a Good Password
The best password I've ever seen was someone that memorized a Windows license key and moved the sections around. Almost pure randomness, but ordered enough to remember. There are easier ways, and things you already know. For instance, do you know your car's license plate? Know the plates of previous cars? Combine them in a memorable fashion, such as breaking them in half and merging two plates together.
 Another
popular method is to take two longish words and misspell them. That would result in
something like "twinkel%unihorn" or "rut]row" or the like.
Easy to remember and hard to guess.
Another
popular method is to take two longish words and misspell them. That would result in
something like "twinkel%unihorn" or "rut]row" or the like.
Easy to remember and hard to guess.
If that's too simple for you, Keychain Access has a tool that helps make passwords, but since there's no emotional investment in them they can be hard to remember (though, there is a phonetic method that makes near-English words as passwords). To get there pick New Password Item from the File menu and click on the lock icon (just one way; there are other ways to get to the assistant).
Rule #0: Never Lose Physical Control
This is at the end so you can remember it, but it's the top concern for security. Do not lose physical control of your computer. Do not leave it somewhere unattended. Do not walk away without locking it down. Do not let someone you don't know use your account to do something like browse the web. Use Fast User Switching and get to a dummy account for things like that. Your account is yours, and that's how you keep your stuff yours.
Another Resource
Apple has a very good guide on hardening Mac OS X in their Common Criteria[4] tools. Download them, do not install them, but read the PDF. There are a ton of tips on how to lock the system down in there.
And there are other published resources such as “Mac OS X Maximum Security”[5].

